To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Aircrack is one of the most popular tools for WEP/WPA/WPA2 cracking. In the new version of Kali (2.0) wich you are most likely using, Wifite has a bug because of wich capturing the handshake fails. In the newest version of wifite this is fixed, but in Kali, the update-function of Wifite (wifite -update i think) won't find the newest version.
hcxtools Description
Small set of tools convert packets from captures (h = hash, c = capture, convert and calculate candidates, x = different hashtypes) for the use with latest hashcat or John the Ripper. The tools are 100% compatible to hashcat and John the Ripper and recommended by hashcat. This branch is pretty closely synced to hashcat git branch (that means: latest hcxtools matching on latest hashcat beta) and John the Ripper git branch ('bleeding-jumbo').
Support for hashcat hash-modes: 2500, 2501, 4800, 5500, 12000, 16100, 16800, 16801
Support for John the Ripper hash-modes: WPAPSK-PMK, PBKDF2-HMAC-SHA1, chap, netntlm, tacacs-plus
Homepage: https://github.com/ZerBea/hcxtools
Author: ZerBea
License: MIT
hcxtools Help
hcxtools is a common name of a set of tools, each executes only one specific function, and each has option set.
hcxpcaptool Help
hcxpcaptool shows info of pcap/pcapng file and convert it to other hashformats accepted by hashcat and John the Ripper.
usage:
options:
bitmask for message pair field:
- 0: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
- 1: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
- 2: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
- 3: x (unused)
- 4: ap-less attack (set to 1) - no nonce-error-corrections neccessary
- 5: LE router detected (set to 1) - nonce-error-corrections only for LE neccessary
- 6: BE router detected (set to 1) - nonce-error-corrections only for BE neccessary
- 7: not replaycount checked (set to 1) - replaycount not checked, nonce-error-corrections definitely neccessary
Do not use hcxpcaptool in combination with third party cap/pcap/pcapng cleaning tools!
hcxpsktool Help
hcxpsktool calculates candidates for hashcat based on commandline input, hccapx file and/or 16800 hash file (experimental).
usage:
options:
hcxhashcattool Help
hcxhashcattool calculate PMKs from hashcat -m 2500 potfile.
usage:
options:
wlanhcx2cap Help
wlanhcx2cap converts hccapx to cap.
usage:
options:
wlanhc2hcx Help
wlanhc2hcx converts hccap to hccapx.
usage:
options:
wlanwkp2hcx Help
wlanwkp2hcx converts wpk (ELMCOMSOFT EWSA projectfile) to hccapx.
usage:
options:
wlanhcx2essid Help
wlanhcx2essid merges hccapx containing the same ESSID.

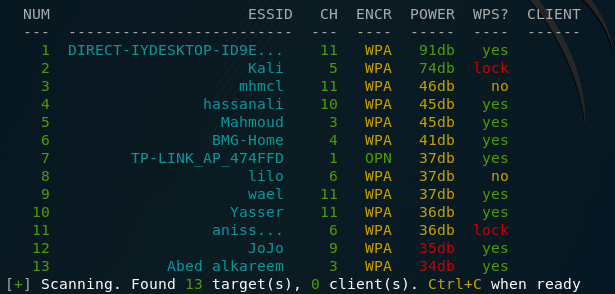
Kali Wifite Handshake Locations
usage:
options:
wlanhcx2ssid Help
wlanhcx2ssid strips BSSID, ESSID, OUI.
usage:
options:
wlanhcxinfo Help
wlanhcxinfo shows detailed info from contents of hccapxfile.
usage.:
options:
wlanhcxmnc Help
wlanhcxmnc help to calculate hashcat's nonce-error-corrections value on byte number xx of an anonce.
usage:
options:
wlanhashhcx Help
wlanhashhcx generate hashlist from hccapx hashfile (md5_64 hash:mac_ap:mac_sta:essid).
usage:
options:
wlanhcxcat Help
wlanhcxcat is a simple password recovery tool for WPA/WPA2/WPA2 SHA256 AES-128-CMAC (hash-modes 2500, 2501).
usage:
options:
input option matrix
wlanpmk2hcx Help
wlanpmk2hcx converts plainmasterkey and ESSID for use with hashcat hash-mode 12000 or john PBKDF2-HMAC-SHA1.
usage:
options:
wlanjohn2hcx Help
wlanjohn2hcx converts john wpapsk hashfiles for use with hashcat hash-modes 2500, 2501.
usage:
options:
wlancow2hcxpmk Help
wlancow2hcxpmk converts pre-computed cowpatty hashfiles for use with hashcat hash-mode 2501.
usage:
options:
wlanhcx2john Help

wlanhcx2john converts hccapx to format expected by John the Ripper.
usage:
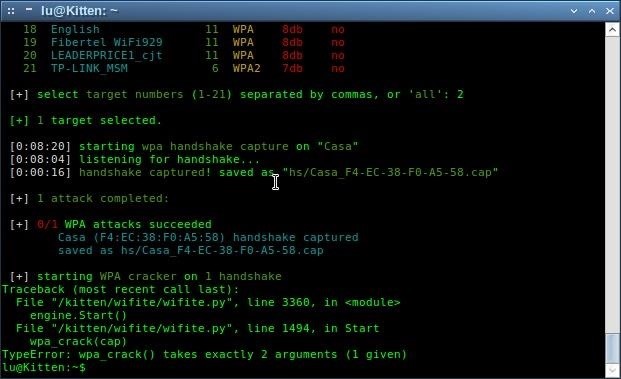
Kali Wifite Handshake Location
options:
wlanhcx2psk Help
wlanhcx2psk calculates candidates for hashcat based on the hccapx file (deprecated: will be replaced by hcxpsktool, soon).
usage:
options:
wlancap2wpasec Help
wlancap2wpasec uploads multiple caps to https://wpa-sec.stanev.org.
usage:
options:
whoismac Help
whoismac shows vendor information and/or download oui reference list.
usage:
options:
hcxtools Usage Example
Show detailed description of hashcat hashfile (NPAAE.hccapx):
Example output:
Show the hash list (format md5_64 hash:mac_ap:mac_sta:essid) of a file (NPAAE.hccapx):
Example output:
Read the file test.pcapng and create the test.16800 file of the PMKID hash for hacking into hashcat with hash mode -m 16800 (-z test.16800):
Example output:
How to install hcxtools
Installation on Kali Linux
Installation on BlackArch
Installation on Debian, Linux Mint, Ubuntu and their derivatives
Screenshots
Tutorials
Related tools
- WiFite (51.2%)
- mdk3 (51.2%)
- Aircrack-ng (Suite of Tools) (51.2%)
- Aircrack-ng (Tool) (51.2%)
- infernal-twin (51.2%)
- wifiphisher (RANDOM - 51.2%)
Recommended for you:
Troubleshooting and fixing issues with Wifi (specifically Wifite) on Kali Linux.
Need help? Join my Discord: https://discord.com/invite/usKSyzb
Commands:
hcxdumptool:
sudo apt install hcxdumptool
hcxpcaptool:
apt install hcxtools
pyrit:
sudo apt-get install libpcap-dev
sudo apt-get install python2.7-dev libssl-dev zlib1g-dev libpcap-dev
git clone https://github.com/JPaulMora/Pyrit.git
cd Pyrit
sudo python setup.py clean
sudo python setup.py build
sudo python setup.py install
Menu:
Overview: 0:00
Exception: airmon-ng did not find wifi interfaces: 0:25
Need to use sudo: 1:17
Missing software: 1:40
Verify Interent connectivity: 2:09
Update references: 2:17
Virtual Machine settings: 2:25
hcxdumptool: 3:07
hcxtools: 3:35
pyrit: 3:48
Test wifite: 6:08
wifite wpa kill: 6:29
Bypass wifite attacks: 8:10
Password: 9:30
Links:
Wifite: https://github.com/derv82/wifite2
Alfa AWUS036NHA: https://amzn.to/3qbQGKN
Alfa AWUSO36NH: https://amzn.to/3moeQiI
Connect with me:
Discord: http://discord.davidbombal.com
Twitter: https://www.twitter.com/davidbombal
Instagram: https://www.instagram.com/davidbombal
LinkedIn: https://www.linkedin.com/in/davidbombal
Facebook: https://www.facebook.com/davidbombal.co
TikTok: http://tiktok.com/@davidbombal
YouTube: https://www.youtube.com/davidbombal
Support me:
Join thisisIT: https://bit.ly/thisisitccna
Or, buy my CCNA course and support me:
DavidBombal.com: CCNA ($10): http://bit.ly/yt999ccna
Udemy CCNA Course: https://bit.ly/ccnafor10dollars
GNS3 CCNA Course: CCNA ($10): https://bit.ly/gns3ccna10
Special Offers:
Cisco Press: Up to 50% discount
Save every day on Cisco Press learning products! Use discount code BOMBAL during checkout to save 35% on print books (plus free shipping in the U.S.), 45% on eBooks, and 50% on video courses and simulator software. Offer expires December 31, 2020. Shop now.
Link: bit.ly/ciscopress50
ITPro.TV:
https://itpro.tv/davidbombal
30% discount off all plans Code: DAVIDBOMBAL
Boson software: 15% discount
Link: bit.ly/boson15
Code: DBAF15P
Kali Wifite Handshake Location Code
wifi
kali
wifi
kali linux 2020
kali linux 2020.4
wifite
wifite2
wifite2 kali linux
wpa
wep
wps
alfa
comptia
cech
oscp
Please note that links listed may be affiliate links and provide me with a small percentage/kickback should you use them to purchase any of the items listed or recommended. Thank you for supporting me and this channel!
#kalilinux #wifi #wifite